3 minutes
Sektor 7: Malware Development Essentials - Review
This is a review over the https://institute.sektor7.net/ “RED TEAM Operator: Malware Development Essentials Course”.
The course is split up into the following sections:
- Portable Executable (PE)
- Droppers
- Obfuscation and Hiding
- Backdoors and Trojans
- Code Injection
- Combined Project
I won’t go over what you learn in depth. If you want to know that just take the course 😉. This review is about my thoughts on the course.
Overall Thoughts: I strongly believe that the concepts taught in this course is fundamental to Red Teaming, Malware Development, and even Malware Analysis. I would recommend this course for anyone interested in malware, red teaming, or just wants to be a better pentester.
Portable Executable
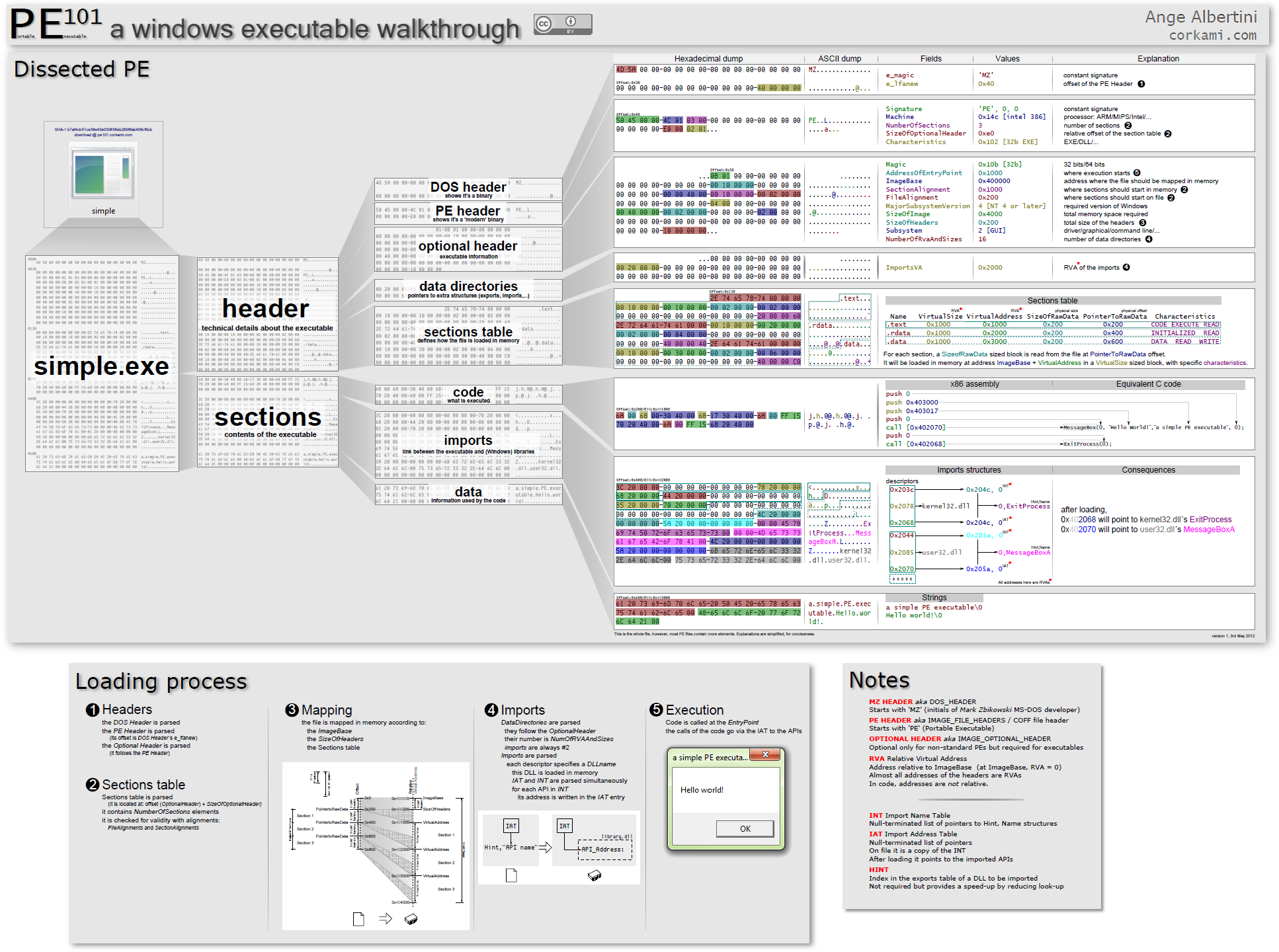
This section is about the Portable Executable (PE) file format which is absolutely crucial to understand if you want to actually understand what is going on in the remainder of the course. Some portions of the course may seem obvious depending on your experience and skill level, e.g. EXE vs DLL, but overall the author of the course did a wonderful job at conveying the information that you absolutely need to know to make your own implants later on down the line. My only real complaint is that I wish the author of the course would leave more “homework” for the student throughout the course. The author kindly has some batch scripts made that come with the course for things like compilation and I think small things like that could be left to the student.
Droppers
Droppers are special programs which are used to deliver your payload (shellcode) to the target machine. This section builds on the previous one as you will need to understand the Portable Executable structure. By this point the author of the course has also given you code templates and the “normal” order of operations for executing shellcode. I won’t spoil the whole thing but it’s just Windows API calls to functions like VirtualAlloc, etc. The thing that blew my mind the most was how a resource section in a PE can hold other PEs! PEception! Although it makes sense since when you statically compile a binary it will need to have everything it needs like other DLLs, etc.
Obfuscation and Hiding

This is where things start to get interesting. Everything from simple Base64 encoding to AES encryption to function call obfuscation. Learning about the insides of how XOR and AES encryption work was not something I imagined going into this course but now encryption makes slightly more sense. The function call obfuscation was a cool Import Address Table trick also. If you went into this like myself and don’t know how the fuck AES works, then this course gives you the best reason to learn how to implement it. Yes, you can just copy and paste from StackOverflow some undergrad CS student’s answer but you’re only cheating yourself.
Backdoors and Trojans

Gone spelunking! Code caves, and sections. This section is all about methods of implanting your own code into an already working binary. So you add your own evil shellcode to Putty so it’s “trojanized”. The cool part is that Putty will still work as normal!
Code Injection
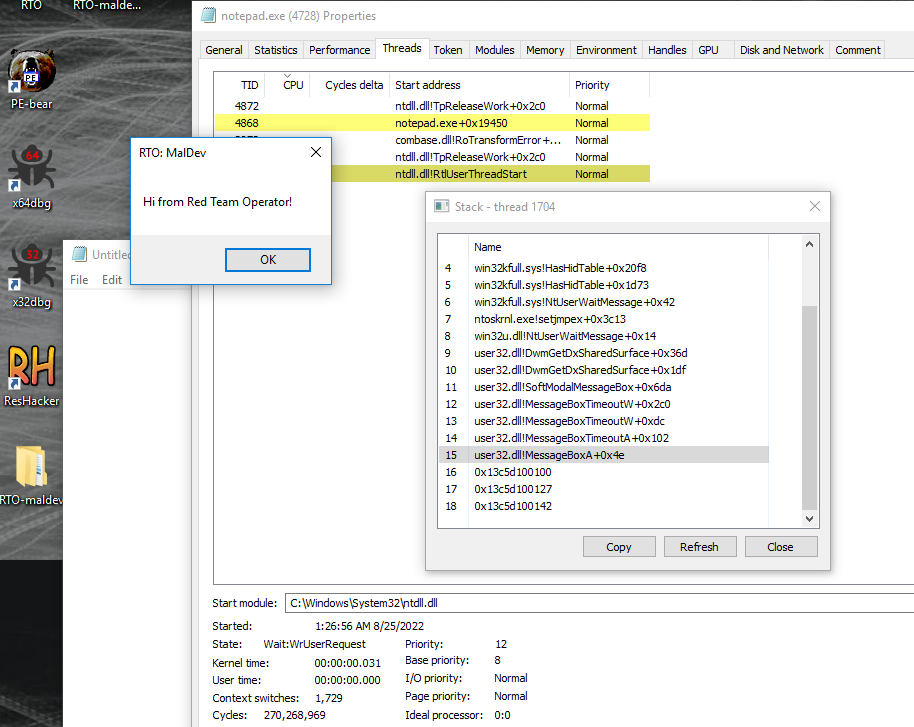
Code Injection is simply a method of transferring your payload from one process to another. Only the “classic” methods of code injection are discussed:
- Shellcode / payload injection w/debugging Win API
- DLL Injection
Combined Project
For the final project in this course, the student will create a dropper which will decrypt the payload from resources section and inject it into explorer.exe. I chose to do it in Golang (still a work in progress) and you can find the source code for it at my Github here Go Dropper